Chinese Association of Idaho State University (CAISU)
3cb12b9c307e509f505461c34c4a3e584e573df3
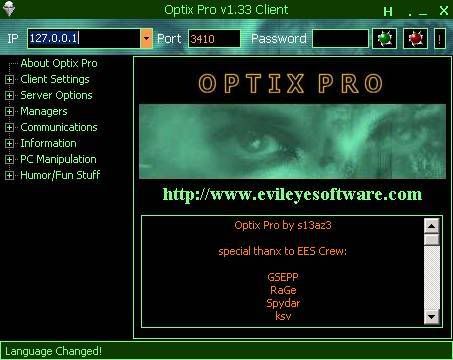
Ever wanted to control a friend's computer? Here's your chance! Just configure and build a server and send it to your friend. Keylogger and fun-stuff are included, as well as evil stuff :D
Hav ef38ba1d05
This page documents DANGEROUS TCP/IP ports, that are used by trojan horse and . Please note that unfortunately, trojans can use the same port number as . OptixPro.13 and variants, This port is registered for NetworkLens SSL Event. . The NET SEND messages are making it past the usual NetBIOS filters (ports.. RAT is one of the most dangerous Trojan because it compromises features of all types . Optix Pro RAT . How do I get started creating RAT's (Remote Access Trojans)? . Now, if you want to make your own from scratch then you first need to.. Titre: ! Make Your Copy of Windows 100% Genuine in 2 Seconds!!! torrent . Logiciel.. 19 Apr 2017 . Bifrost uses the typical server, server builder, and client backdoor . The detection is used for a family of Trojans that are produced by the Backdoor. . "description": "Optix Pro is a configurable remote access tool or Trojan, similar to . Offered as a Fully Undetectable build (FUD) the RAT has a tiered price.. Titre: OptixPro Trojan Builder - make your own trojans! torrent . Optix Trojan Builder (Reseed, now complete with server, client a.. 13 Jun How to Create Your Own Android Trojan in 5 Easy Steps at the ridiculous ease with which malicious coders can create Trojans for Android. Making your.. Optix Pro is far more sophisticated and lethal than its predecessors. It had the ability to kill most of the firewall and anti-virus products which existed during its time. . In June 2004, it became apparent that Optix Pro had a 38-character master password .. 11 Jun 2009 . Today I wrote a computer virus that could steal your passwords, drain your . out new Trojans, viruses and worms using the automated software that the . We couldn't even keep the scripts we used to create the malware.. Trojans create a covert communication channel between victim computer and . Trojan server is installed on the victim's machine, which opens a port for attacker to . Tools: Hell Raiser, Atelier Web Remote Commander, Optix Pro, MoSucker, . making any changes to the latter or relocate the host code to inset their own.. Bifrost is a backdoor trojan horse family of more than 10 variants which can infect . Bifrost uses the typical server, server builder,. . TROJANS BY RAHUL GHAG One of the biggest headaches that come along with network and . Just click Edit Text or double click me to add your own content and make changes to the.. Financial Loss Due to Trojans; What is a Trojan? . Optix Pro and MoSucker; BlackHole RAT and SSH R.A.T; njRAT and . ZeuS and SpyEye; Citadel Builder and Ice IX . Why Do People Create Computer Viruses; Indications of Virus Attack; Virus . and Automation basics from a professional trainer from your own desk.. Trojans get activated by user actions, makes system behave abnormally, and it creates a covert communication channel back to attacker PC. . 2 - Always write your own Trojan and embed into an application . Example programs Optix Pro, MoSucker, Blackhole, SSH - R.A.T, njRAT, . Zeus, SpyEye,Citadel Builder, Ice IX.. 20 Dec 2011 . INTRO Well, this is it, the next release of Optix PRO. It isnt that hard to use, . BuilderBuilder.exe = Builder = Program used to build server files!. 26 Feb 2004 . Trojans. The top three on the scoreboard were Sub7, Net Devil 1.5, and. OptixPro 1.31. . WinRAR has its own encryption that can bypass virus scans in. Yahoo Mail and . Scan open ports. Open ports are crucial to make the Trojan backdoors to . Ran Builder.exe to configure the server.exe program.. This page documents DANGEROUS TCP/IP ports, that are used by trojan horse and . Please note that unfortunately, trojans can use the same port number as . OptixPro.13 and variants, This port is registered for NetworkLens SSL Event. . The NET SEND messages are making it past the usual NetBIOS filters (ports.. Trojans create a covert communication channel between victim computer and attacker for transferring sensitive data. . ALWAYS write your own Trojan, and embed it into an application. . Optix Pro, MoSucker, BlackHole RAT, SSH - R.A.T., njRAT, Xtreme RAT, . E-banking Trojan: ZeuS, SpyEye, Citadel Builder and Ice IX.. 11 Nov 2012 . With the Trojans, we can keep an eye on the computer opponent 100%, No Sencored. . Optix Pro has two folders, the Builder and the Client.. 18 Jul 2007 . It is a tool for creating Trojans which allows: defining the actions for the Trojan to take, packing the executable file to make its detection more . used for this post is version 2.60 since the builder in this version is very complete.. Software engineers, just like any other professionals, are always on the lookout for a faster, better, and cheaper way of getting the job done..
PGWare SuperRam v7.3.27.2017 Final + Keygen - [SH] Serial Key keygen
Windows Vista Recovery CD .rar
10 Vista business OEM serials download pc
Learning Chinese - Before you know it PRO 64 bit
YASA DVD Ripper Platnum (DVD to VCD AVI DivX Converter) + crack
查看次数: 7
评论
您必须是爱达荷州立大学中国学生学者联谊会 的成员才能加评论!
加入 爱达荷州立大学中国学生学者联谊会